GDB
run with argv
gdb —args {name} {argv[1], argv[2], …. }
ex:
1
| gdb --args ./main arg1 arg2
|
x/nuf [address]
n: repeat count
u: unit size
| u |
unit size (byte) |
| b |
1 |
| h |
2 |
| w |
4 |
| g |
8 |
f: display format
| f |
format |
| x |
hex |
| d |
int |
| s |
string |
| i |
instruction |
otehr command
| x |
command |
| run until this function end |
return |
| run until breakpoint |
continue |
| finish this process |
finish |
| clear the screen |
clear |
| set environment variable |
set env {var} {value} |
| exit |
q |
set environment variable
set env {var} {value}
1
| set env LD_PRELOAD ./libc.so
|
peda and pwngdb
pwngdb github: https://github.com/scwuaptx/Pwngdb
peda github: https://github.com/longld/peda
| x |
command |
| check section info |
vmmap |
| show heap info |
heapinfo |
| some useful data |
magic |
| show got table |
got |
| show rop gadget |
rop |
| show libc address |
libc |
| generate shellcode |
shellcode generate x86/linux exec |
set register
set ${register}=value
ex:
IDA pro
cheatsheet
IDA Pro shortcuts
| x |
command |
| disassemble |
press ‘F5’ |
| cross reference |
select the function and press ‘x’ |
| Mark var name |
select the var and press ‘n’ |
| Mark type |
select the var and press ‘y’ |
patch binary
- Edit -> Patch program -> assemble
- Edit -> Patch program -> Apply patches to input file
common static analysis command
readelf
1
| readelf -s /lib/x86_64-linux-gnu/libc-2.27.so | grep __libc_start_main
|
objdump
show assembly code
1
2
3
4
5
| # see got table:
objdump -R {binary}
# see assembly code:
objdump -D {binary}
|
checksec
check protection mechanism
strings
show printable character in binary
file
strace
1
2
3
4
5
| # syscall when running
strace {binary}
# set output length
strace -s {len} {binary}
|
nc / ncat
1
2
3
4
5
| #attach to ip
ncat -vc {binary} -kl {ip} {port}
#connect to ip
nc {ip} {port}
|
shellcode
1
2
3
4
5
| # x86/linux/exec: 24 bytes
shellcode = (
"\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31"
"\xc9\x89\xca\x6a\x0b\x58\xcd\x80"
)
|
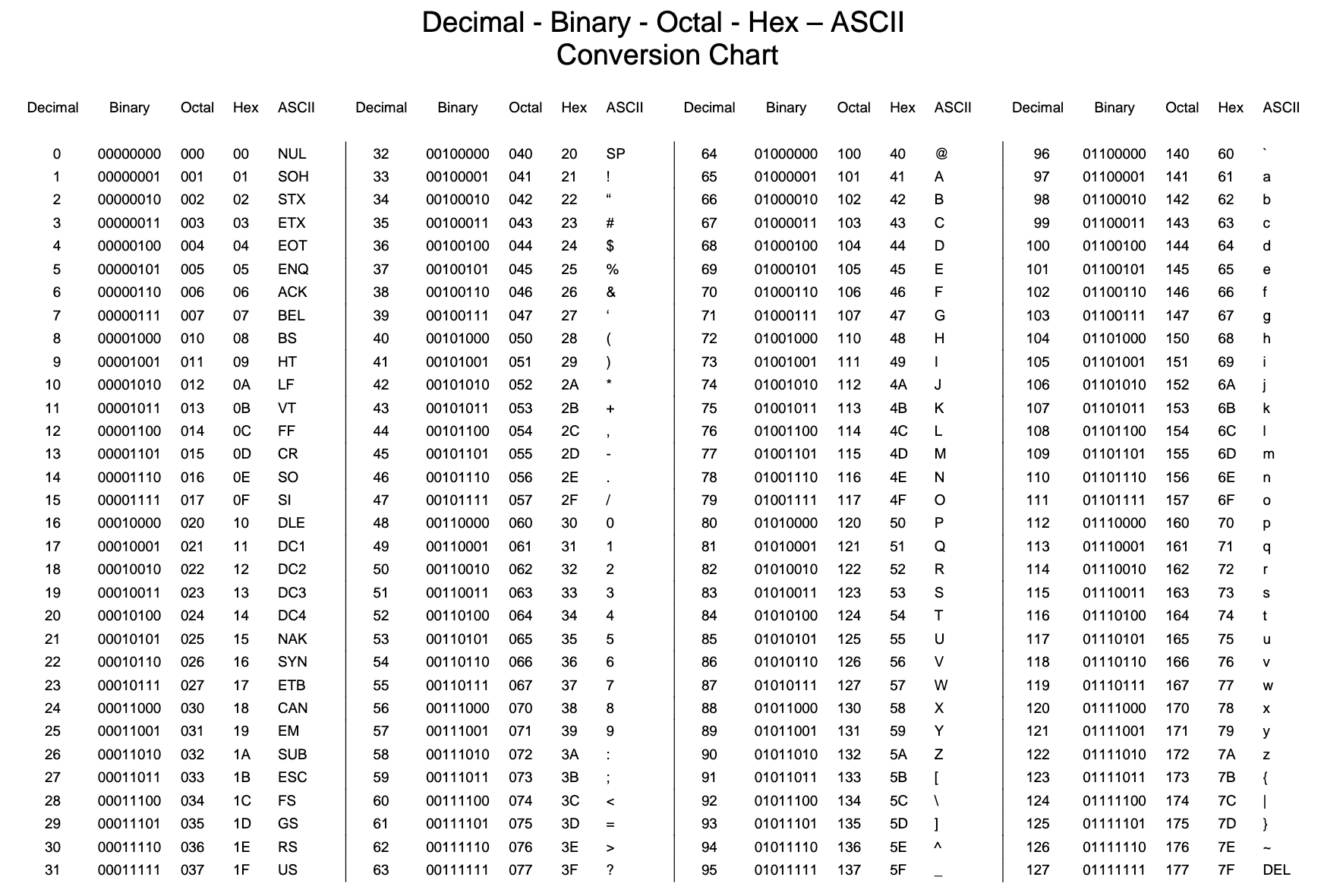
ascii tbl